
Security - Surveillance
Surveillance is the monitoring of any behaviour, activities, or other changing information, usually of people for the purpose of influencing, managing, directing, or protecting them. This can include observation from a distance by means of electronic equipment such as a CCTV.
Now, Video surveillance systems are increasingly being used in security systems and with good reason. Even the presence of video cameras acts as a deterrent to potential criminals. Possible dangers are also detected at any early stage. Appropriate and rapid intervention will enable damage at least to be contained. Given the ever-growing sources of danger and increasing losses, video surveillance is an extremely valuable and economical means of improving the security of people, buildings, and valuables.
Information Security & Availability
Information security is the practice of defending information from unauthorized access, use, disclosure, disruption, modification, perusal, inspection, recording or destruction. Ensuring that information systems and the necessary data are available for use when they are needed.
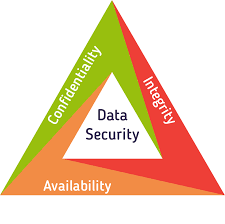
Few major aspects of information security & availability are:
Availability
Assurance that the systems responsible for delivering, storing and processing information are accessible when needed, by those who need them. Availability was thus the poor relation of Confidentiality and Integrity in security terms. However, the extension of the working day (for example because of trading with different time zones) and the growth of 24×7 systems, associated with e.g. web sites, Internet (on-line) trading, cash point machines, coupled with the threats of viruses and intrusions means that availability has become a much more important element of Information Security work.
Confidentiality
Assurance that information is shared only among authorised persons or organisations. Breaches of Confidentiality can occur when data is not handled in a manner adequate to safeguard the confidentiality of the information concerned. Such disclosure can take place by word of mouth, by printing, copying, e-mailing, or creating documents and other data etc. The classification of the information should determine is confidentiality and hence the appropriate safeguards.
Integrity
Assurance that the information is authentic and complete. Ensuring that information can be relied upon to be sufficiently accurate for its purpose. The term Integrity is used frequently when considering Information Security as it is representing one of the primary indicators of security (or lack of it). The integrity of data is not only whether the data is ‘correct’, but whether it can be trusted and relied upon. For example, making copies (say by e-mailing a file) of a sensitive document, threatens both confidentiality and the integrity of the information. Why? Because, by making one or more copies, the data is then at risk of change or modification.

IT Security
Sometimes referred to as security of systems, Information Technology Security is information security applied to technology. The field covers all the processes and mechanisms by which computer-based equipment, information and services are protected from unintended or unauthorized access, change or destruction. Computer security also includes protection from unplanned events and natural disasters.
Information Assurance
The act of ensuring that data is not lost when critical issues arise. These issues include but are not limited to natural disasters, computer/server malfunction, physical theft, or any other instance where critical data has the potential of